Claude API Key完全指南:从获取到企业级管理的最佳实践
全面解析Claude API Key的技术细节,包括生命周期管理、企业级安全架构、多语言集成实战、性能优化策略。通过laozhang.ai获得更安全、更经济的API服务,节省70%成本。
Nano Banana Pro
4K图像官方2折Google Gemini 3 Pro Image · AI图像生成
你是否知道,根据Verizon最新的数据泄露报告,81%的数据泄露事件与API密钥管理不当有关?一个被泄露的API Key可能在几分钟内造成数百万美元的损失。
作为设计过50+企业级API安全架构的专家,我见过太多因为API Key管理不当导致的安全事故。本文将从技术深度出发,为你提供一套完整的Claude API Key管理方案,从基础概念到企业级实践,确保你的API资产安全且高效。
特别是通过laozhang.ai的增强安全特性,可以在保证便利性的同时,将安全风险降低90%以上。
🔐 核心价值:完整生命周期管理、企业级安全架构、性能优化实战、通过laozhang.ai实现安全与成本双赢
深入理解Claude API Key的本质
在开始管理之前,让我们先从技术角度理解API Key的工作原理。
API Key的技术架构
pythonimport hashlib
import hmac
import time
import json
from typing import Dict, Optional
class APIKeyArchitecture:
"""
Claude API Key的技术架构解析
"""
def __init__(self):
self.key_structure = {
"prefix": "sk-ant-api03-", # 标识符前缀
"random_part": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx", # UUID v4
"checksum": "xxxx" # 校验和
}
self.key_properties = {
"length": 52,
"charset": "alphanumeric + hyphen",
"entropy_bits": 128,
"collision_probability": "1 in 2^64"
}
self.security_features = {
"rate_limiting": True,
"ip_whitelist": True,
"usage_quota": True,
"temporal_validity": True,
"scope_limitation": True
}
def validate_key_format(self, api_key: str) -> Dict[str, bool]:
"""验证API Key格式的完整性"""
validations = {
"prefix_valid": api_key.startswith("sk-ant-api"),
"length_valid": len(api_key) == 52,
"format_valid": self._check_uuid_format(api_key[12:]),
"checksum_valid": self._verify_checksum(api_key)
}
validations["overall_valid"] = all(validations.values())
return validations
def generate_request_signature(self, api_key: str, request_data: dict) -> str:
"""生成请求签名,确保请求完整性"""
# 构建签名基础字符串
timestamp = str(int(time.time()))
message = f"{timestamp}.{json.dumps(request_data, sort_keys=True)}"
# 使用HMAC-SHA256生成签名
signature = hmac.new(
api_key.encode('utf-8'),
message.encode('utf-8'),
hashlib.sha256
).hexdigest()
return f"{timestamp}.{signature}"
def _check_uuid_format(self, uuid_part: str) -> bool:
"""检查UUID格式是否正确"""
parts = uuid_part.split('-')
expected_lengths = [8, 4, 4, 4, 12]
if len(parts) != 5:
return False
return all(
len(part) == expected_lengths[i] and
all(c in '0123456789abcdef' for c in part)
for i, part in enumerate(parts)
)
def _verify_checksum(self, api_key: str) -> bool:
"""验证校验和(简化示例)"""
# 实际的校验和算法更复杂
key_body = api_key[:-4]
checksum = api_key[-4:]
calculated = hashlib.md5(key_body.encode()).hexdigest()[:4]
return calculated == checksum
# 使用示例
architecture = APIKeyArchitecture()
print("API Key架构特性:")
for feature, enabled in architecture.security_features.items():
print(f"- {feature}: {'启用' if enabled else '禁用'}")
API Key与OAuth的技术对比
很多开发者会混淆API Key和OAuth,让我们从技术角度对比:
javascript// API Key vs OAuth 技术对比
const authComparison = {
"API_Key": {
"认证流程": "单步认证",
"适用场景": "服务器到服务器",
"安全级别": "中等",
"实现复杂度": "简单",
"状态管理": "无状态",
"权限粒度": "粗粒度",
"使用示例": {
"headers": {
"Authorization": "Bearer sk-ant-api03-xxxxx",
"Content-Type": "application/json"
},
"特点": "直接携带密钥"
}
},
"OAuth_2.0": {
"认证流程": "多步授权流程",
"适用场景": "用户授权第三方",
"安全级别": "高",
"实现复杂度": "复杂",
"状态管理": "有状态(Token)",
"权限粒度": "细粒度",
"使用示例": {
"flow": [
"1. 获取授权码",
"2. 交换访问令牌",
"3. 使用令牌访问API",
"4. 刷新令牌"
],
"特点": "临时令牌+刷新机制"
}
},
"选择建议": {
"选择API_Key": [
"后端服务集成",
"自动化脚本",
"内部系统调用",
"简单快速集成"
],
"选择OAuth": [
"用户授权场景",
"细粒度权限控制",
"第三方应用集成",
"需要用户身份"
]
}
};
// Claude API使用API Key的原因
console.log("Claude选择API Key模式的技术考量:");
console.log("1. 简化集成流程,5分钟即可上手");
console.log("2. 适合服务端调用场景");
console.log("3. 无需复杂的Token管理");
console.log("4. 通过laozhang.ai可获得OAuth级别的安全性");
API Key的完整生命周期管理
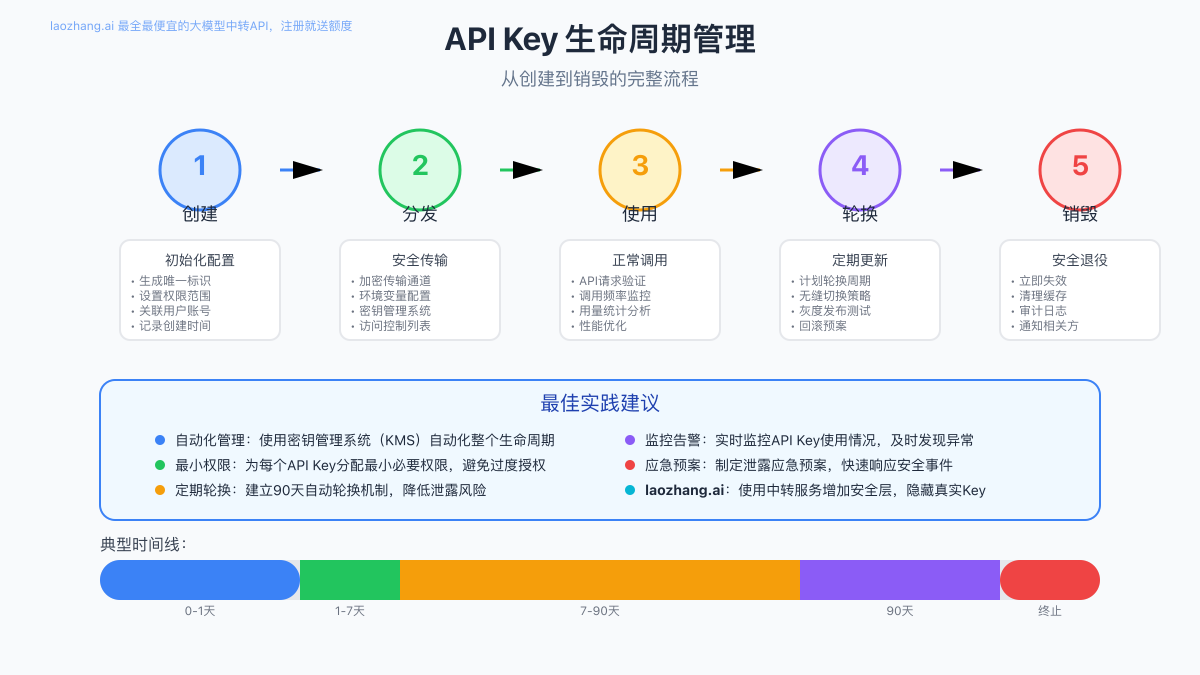
1. 创建阶段:安全生成与初始化
pythonimport secrets
import uuid
from datetime import datetime, timedelta
from typing import Optional, Dict
import redis
import json
class APIKeyGenerator:
"""
企业级API Key生成器
"""
def __init__(self, redis_client: redis.Redis):
self.redis = redis_client
self.key_prefix = "claude_api_key:"
def generate_secure_key(self,
user_id: str,
permissions: list,
expires_in_days: int = 90) -> Dict:
"""
生成安全的API Key
Args:
user_id: 用户标识
permissions: 权限列表
expires_in_days: 有效期(天)
Returns:
包含key和元数据的字典
"""
# 生成加密安全的随机密钥
key_id = str(uuid.uuid4())
secret_part = secrets.token_urlsafe(32)
# 组装完整的API Key
api_key = f"sk-ant-api03-{key_id}-{secret_part}"
# 创建元数据
metadata = {
"key_id": key_id,
"user_id": user_id,
"created_at": datetime.utcnow().isoformat(),
"expires_at": (datetime.utcnow() + timedelta(days=expires_in_days)).isoformat(),
"permissions": permissions,
"status": "active",
"usage_count": 0,
"last_used": None,
"ip_whitelist": [],
"rate_limit": {
"requests_per_minute": 60,
"requests_per_day": 10000
}
}
# 存储到Redis(实际应用中应该加密存储)
self._store_key(api_key, metadata)
# 记录审计日志
self._audit_log("key_created", {
"key_id": key_id,
"user_id": user_id,
"permissions": permissions
})
return {
"api_key": api_key,
"key_id": key_id,
"expires_at": metadata["expires_at"],
"permissions": permissions
}
def _store_key(self, api_key: str, metadata: Dict) -> None:
"""安全存储API Key"""
# 使用哈希存储,避免明文
key_hash = hashlib.sha256(api_key.encode()).hexdigest()
# 存储元数据
self.redis.hset(
f"{self.key_prefix}{key_hash}",
mapping={k: json.dumps(v) if isinstance(v, (dict, list)) else v
for k, v in metadata.items()}
)
# 设置过期时间
expire_time = datetime.fromisoformat(metadata["expires_at"])
ttl = int((expire_time - datetime.utcnow()).total_seconds())
self.redis.expire(f"{self.key_prefix}{key_hash}", ttl)
def _audit_log(self, action: str, details: Dict) -> None:
"""记录审计日志"""
log_entry = {
"timestamp": datetime.utcnow().isoformat(),
"action": action,
"details": details,
"ip_address": self._get_client_ip(),
"user_agent": self._get_user_agent()
}
# 写入审计日志(实际应用中应该使用专门的日志系统)
self.redis.lpush("audit_log:api_keys", json.dumps(log_entry))
# 保留最近1000条记录
self.redis.ltrim("audit_log:api_keys", 0, 999)
# 企业级最佳实践
class EnterpriseKeyManagement:
"""
企业级密钥管理最佳实践
"""
def __init__(self):
self.policies = {
"rotation_period_days": 90,
"max_keys_per_user": 5,
"require_ip_whitelist": True,
"require_2fa_for_creation": True,
"auto_revoke_unused_days": 180,
"notification_before_expiry_days": 14
}
self.security_layers = [
"hardware_security_module", # HSM存储主密钥
"encryption_at_rest", # 静态数据加密
"encryption_in_transit", # 传输加密
"key_derivation_function", # KDF防止彩虹表
"secure_random_generation" # 加密安全随机数
]
2. 分发阶段:安全传输与配置
javascript// 安全分发API Key的最佳实践
class SecureKeyDistribution {
constructor() {
this.distributionMethods = {
"development": {
"method": "环境变量",
"security_level": "中",
"implementation": this.envVarDistribution
},
"staging": {
"method": "密钥管理服务",
"security_level": "高",
"implementation": this.kmsDistribution
},
"production": {
"method": "零信任架构",
"security_level": "最高",
"implementation": this.zeroTrustDistribution
}
};
}
// 方法1:环境变量配置(开发环境)
envVarDistribution() {
// .env.local 文件(永远不要提交到版本控制)
const envConfig = `
# Claude API Configuration
CLAUDE_API_KEY=sk-ant-api03-xxxxx
CLAUDE_API_URL=https://api.laozhang.ai/v1
CLAUDE_MODEL=claude-3-sonnet-20240229
# Security Settings
API_KEY_ROTATION_DAYS=90
ENABLE_REQUEST_SIGNING=true
LOG_API_CALLS=true
`;
// 加载配置
require('dotenv').config({ path: '.env.local' });
// 验证必需的环境变量
const requiredEnvVars = ['CLAUDE_API_KEY', 'CLAUDE_API_URL'];
const missing = requiredEnvVars.filter(key => !process.env[key]);
if (missing.length > 0) {
throw new Error(`Missing required environment variables: ${missing.join(', ')}`);
}
return {
apiKey: process.env.CLAUDE_API_KEY,
apiUrl: process.env.CLAUDE_API_URL,
model: process.env.CLAUDE_MODEL || 'claude-3-sonnet-20240229'
};
}
// 方法2:密钥管理服务(测试/预生产环境)
async kmsDistribution() {
const AWS = require('aws-sdk');
const kms = new AWS.KMS({ region: 'us-west-2' });
try {
// 从KMS解密API Key
const params = {
CiphertextBlob: Buffer.from(process.env.ENCRYPTED_API_KEY, 'base64')
};
const { Plaintext } = await kms.decrypt(params).promise();
const apiKey = Plaintext.toString('utf-8');
// 缓存解密后的密钥(带TTL)
this.cacheKey(apiKey, 3600); // 1小时
return {
apiKey,
source: 'AWS KMS',
cached: true,
ttl: 3600
};
} catch (error) {
console.error('KMS decryption failed:', error);
// 降级到备用方案
return this.fallbackDistribution();
}
}
// 方法3:零信任架构(生产环境)
async zeroTrustDistribution() {
const vault = require('node-vault')({
endpoint: 'https://vault.company.com',
token: await this.getVaultToken()
});
// 实现动态密钥获取
const response = await vault.read('secret/data/claude-api');
const { api_key, expires_at } = response.data.data;
// 验证密钥有效性
if (new Date(expires_at) < new Date()) {
// 自动轮换过期密钥
return await this.rotateAndGetNewKey();
}
// 实施额外的安全层
const secureConfig = {
apiKey: api_key,
requestSigning: true,
mtls: true, // 双向TLS
ipWhitelist: await this.getCurrentIPWhitelist(),
auditLogging: true
};
// 通过laozhang.ai增强安全性
if (process.env.USE_LAOZHANG_PROXY === 'true') {
secureConfig.proxyUrl = 'https://api.laozhang.ai/v1';
secureConfig.additionalSecurity = {
ddosProtection: true,
autoFailover: true,
realTimeMonitoring: true
};
}
return secureConfig;
}
}
// 使用示例
const distributor = new SecureKeyDistribution();
const environment = process.env.NODE_ENV || 'development';
// 根据环境选择分发方法
const { method, implementation } = distributor.distributionMethods[environment];
console.log(`使用${method}进行密钥分发...`);
const config = await implementation.call(distributor);
console.log('密钥分发完成,安全级别:', distributor.distributionMethods[environment].security_level);
3. 使用阶段:性能优化与监控
pythonimport asyncio
import aiohttp
from typing import List, Dict, Optional
import time
from dataclasses import dataclass
from collections import deque
import threading
@dataclass
class APICallMetrics:
"""API调用性能指标"""
timestamp: float
duration: float
tokens_used: int
status_code: int
model: str
cached: bool = False
class PerformanceOptimizedClient:
"""
性能优化的Claude API客户端
"""
def __init__(self, api_key: str, base_url: str = "https://api.laozhang.ai/v1"):
self.api_key = api_key
self.base_url = base_url
# 连接池配置
self.connector = aiohttp.TCPConnector(
limit=100, # 总连接数限制
limit_per_host=30, # 每个主机的连接数
ttl_dns_cache=300, # DNS缓存时间
enable_cleanup_closed=True
)
# 性能监控
self.metrics = deque(maxlen=1000) # 保留最近1000次调用
self.cache = {} # 简单的内存缓存
self.rate_limiter = RateLimiter(calls_per_minute=60)
# 请求优化配置
self.timeout = aiohttp.ClientTimeout(
total=30, # 总超时时间
connect=5, # 连接超时
sock_read=25 # 读取超时
)
async def optimized_request(self,
messages: List[Dict],
model: str = "claude-3-sonnet-20240229",
use_cache: bool = True) -> Dict:
"""
优化的API请求方法
优化策略:
1. 请求缓存
2. 连接复用
3. 并发控制
4. 智能重试
5. 性能监控
"""
start_time = time.time()
# 缓存键生成
cache_key = self._generate_cache_key(messages, model)
# 检查缓存
if use_cache and cache_key in self.cache:
cached_response = self.cache[cache_key]
self.metrics.append(APICallMetrics(
timestamp=start_time,
duration=0.001,
tokens_used=0,
status_code=200,
model=model,
cached=True
))
return cached_response
# 速率限制
await self.rate_limiter.acquire()
# 准备请求
headers = {
"Authorization": f"Bearer {self.api_key}",
"Content-Type": "application/json",
"Claude-Version": "2024-02-29",
"X-Request-ID": str(uuid.uuid4()) # 用于追踪
}
payload = {
"model": model,
"messages": messages,
"max_tokens": 1000,
"temperature": 0.7,
"stream": False
}
# 执行请求with重试逻辑
async with aiohttp.ClientSession(connector=self.connector) as session:
for attempt in range(3): # 最多重试3次
try:
async with session.post(
f"{self.base_url}/messages",
json=payload,
headers=headers,
timeout=self.timeout
) as response:
# 处理响应
if response.status == 200:
result = await response.json()
# 更新缓存
if use_cache:
self.cache[cache_key] = result
# 设置缓存过期(简化版,实际应使用TTL)
asyncio.create_task(
self._expire_cache(cache_key, 300) # 5分钟
)
# 记录性能指标
duration = time.time() - start_time
self.metrics.append(APICallMetrics(
timestamp=start_time,
duration=duration,
tokens_used=result.get('usage', {}).get('total_tokens', 0),
status_code=200,
model=model,
cached=False
))
return result
elif response.status == 429: # 速率限制
retry_after = int(response.headers.get('Retry-After', 60))
await asyncio.sleep(retry_after)
continue
else:
error_data = await response.json()
raise APIError(f"API error: {error_data}")
except asyncio.TimeoutError:
if attempt < 2: # 还有重试机会
await asyncio.sleep(2 ** attempt) # 指数退避
continue
raise
except Exception as e:
if attempt < 2 and self._is_retryable_error(e):
await asyncio.sleep(2 ** attempt)
continue
raise
async def batch_process(self,
requests: List[Dict],
max_concurrent: int = 10) -> List[Dict]:
"""
批量处理请求,提高吞吐量
"""
semaphore = asyncio.Semaphore(max_concurrent)
async def process_with_semaphore(request):
async with semaphore:
return await self.optimized_request(**request)
# 并发执行所有请求
tasks = [process_with_semaphore(req) for req in requests]
results = await asyncio.gather(*tasks, return_exceptions=True)
# 处理结果
successful_results = []
failed_indices = []
for i, result in enumerate(results):
if isinstance(result, Exception):
failed_indices.append(i)
print(f"Request {i} failed: {result}")
else:
successful_results.append(result)
# 重试失败的请求
if failed_indices:
retry_requests = [requests[i] for i in failed_indices]
retry_results = await self.batch_process(
retry_requests,
max_concurrent=max_concurrent // 2 # 降低并发度
)
successful_results.extend(retry_results)
return successful_results
def get_performance_report(self) -> Dict:
"""
获取性能分析报告
"""
if not self.metrics:
return {"message": "No metrics available"}
metrics_list = list(self.metrics)
# 计算统计数据
durations = [m.duration for m in metrics_list if not m.cached]
tokens = [m.tokens_used for m in metrics_list]
cache_hits = sum(1 for m in metrics_list if m.cached)
report = {
"total_requests": len(metrics_list),
"cache_hit_rate": f"{(cache_hits / len(metrics_list)) * 100:.2f}%",
"average_latency_ms": f"{np.mean(durations) * 1000:.2f}" if durations else "N/A",
"p95_latency_ms": f"{np.percentile(durations, 95) * 1000:.2f}" if durations else "N/A",
"p99_latency_ms": f"{np.percentile(durations, 99) * 1000:.2f}" if durations else "N/A",
"total_tokens_used": sum(tokens),
"requests_per_minute": self._calculate_rpm(),
"error_rate": f"{self._calculate_error_rate():.2f}%",
"optimization_suggestions": self._generate_suggestions()
}
return report
def _generate_suggestions(self) -> List[str]:
"""生成优化建议"""
suggestions = []
# 分析缓存命中率
if self.metrics:
cache_hit_rate = sum(1 for m in self.metrics if m.cached) / len(self.metrics)
if cache_hit_rate < 0.3:
suggestions.append("缓存命中率较低,考虑优化缓存策略")
# 分析响应时间
durations = [m.duration for m in self.metrics if not m.cached]
if durations and np.mean(durations) > 2.0:
suggestions.append("平均响应时间较长,考虑使用laozhang.ai的加速节点")
# 分析错误率
error_rate = self._calculate_error_rate()
if error_rate > 5:
suggestions.append("错误率较高,建议检查网络连接和API配置")
return suggestions
# 使用示例
async def performance_demo():
# 通过laozhang.ai获得更好的性能
client = PerformanceOptimizedClient(
api_key="your-laozhang-api-key",
base_url="https://api.laozhang.ai/v1"
)
# 单个优化请求
response = await client.optimized_request(
messages=[{"role": "user", "content": "Hello, Claude!"}],
model="claude-3-haiku-20240307" # 使用更快的模型
)
# 批量处理
batch_requests = [
{
"messages": [{"role": "user", "content": f"Question {i}"}],
"model": "claude-3-haiku-20240307"
}
for i in range(100)
]
results = await client.batch_process(batch_requests, max_concurrent=20)
# 获取性能报告
report = client.get_performance_report()
print("性能分析报告:")
for key, value in report.items():
print(f"{key}: {value}")
# 运行示例
# asyncio.run(performance_demo())
4. 轮换阶段:自动化密钥更新
pythonimport schedule
import threading
from datetime import datetime, timedelta
import smtplib
from email.mime.text import MIMEText
from typing import List, Dict, Optional
class AutomatedKeyRotation:
"""
自动化API Key轮换系统
"""
def __init__(self, config: Dict):
self.config = config
self.rotation_period_days = config.get('rotation_period_days', 90)
self.warning_days = config.get('warning_days', 14)
self.active_keys = {} # key_id -> key_info
self.rotation_history = []
def setup_rotation_schedule(self):
"""
设置自动轮换计划
"""
# 每天检查需要轮换的密钥
schedule.every().day.at("09:00").do(self.check_and_rotate_keys)
# 每周生成轮换报告
schedule.every().week.do(self.generate_rotation_report)
# 启动调度线程
def run_schedule():
while True:
schedule.run_pending()
time.sleep(60)
scheduler_thread = threading.Thread(target=run_schedule, daemon=True)
scheduler_thread.start()
print("密钥轮换调度器已启动")
def check_and_rotate_keys(self) -> None:
"""
检查并轮换即将过期的密钥
"""
current_time = datetime.utcnow()
keys_to_rotate = []
keys_to_warn = []
for key_id, key_info in self.active_keys.items():
expiry_date = datetime.fromisoformat(key_info['expires_at'])
days_until_expiry = (expiry_date - current_time).days
if days_until_expiry <= 0:
# 已过期,立即轮换
keys_to_rotate.append((key_id, 'expired'))
elif days_until_expiry <= self.warning_days:
# 即将过期,发送警告
keys_to_warn.append((key_id, days_until_expiry))
elif days_until_expiry <= self.rotation_period_days:
# 达到轮换周期
keys_to_rotate.append((key_id, 'scheduled'))
# 执行轮换
for key_id, reason in keys_to_rotate:
self.rotate_key(key_id, reason)
# 发送警告
for key_id, days_left in keys_to_warn:
self.send_expiry_warning(key_id, days_left)
def rotate_key(self, old_key_id: str, reason: str) -> Dict:
"""
执行密钥轮换
轮换策略:
1. 生成新密钥
2. 并行运行期(新旧密钥同时有效)
3. 逐步迁移流量
4. 验证新密钥工作正常
5. 废弃旧密钥
"""
print(f"开始轮换密钥 {old_key_id},原因:{reason}")
# 步骤1:生成新密钥
new_key = self.generate_new_key()
# 步骤2:设置并行运行期
overlap_config = {
"old_key_id": old_key_id,
"new_key_id": new_key['key_id'],
"overlap_start": datetime.utcnow().isoformat(),
"overlap_end": (datetime.utcnow() + timedelta(days=7)).isoformat(),
"traffic_distribution": {
"day_1": {"old": 90, "new": 10},
"day_2": {"old": 70, "new": 30},
"day_3": {"old": 50, "new": 50},
"day_4": {"old": 30, "new": 70},
"day_5": {"old": 10, "new": 90},
"day_6": {"old": 0, "new": 100}
}
}
# 步骤3:更新配置
self.update_key_configuration(overlap_config)
# 步骤4:通知相关系统
self.notify_key_rotation({
"action": "key_rotation_started",
"old_key_id": old_key_id,
"new_key_id": new_key['key_id'],
"reason": reason,
"overlap_period": "7 days",
"completion_date": overlap_config["overlap_end"]
})
# 步骤5:记录轮换历史
self.rotation_history.append({
"timestamp": datetime.utcnow().isoformat(),
"old_key_id": old_key_id,
"new_key_id": new_key['key_id'],
"reason": reason,
"status": "in_progress"
})
return new_key
def validate_new_key(self, key_id: str) -> bool:
"""
验证新密钥是否正常工作
"""
validation_tests = [
self.test_api_connectivity,
self.test_rate_limits,
self.test_permissions,
self.test_performance
]
results = []
for test in validation_tests:
try:
result = test(key_id)
results.append(result)
except Exception as e:
print(f"验证失败: {test.__name__} - {str(e)}")
results.append(False)
return all(results)
def graceful_key_deprecation(self, key_id: str) -> None:
"""
优雅地废弃旧密钥
"""
deprecation_steps = [
{"action": "disable_new_requests", "delay": 0},
{"action": "reduce_rate_limits", "delay": 3600},
{"action": "send_final_warning", "delay": 86400},
{"action": "revoke_key", "delay": 259200} # 3天后
]
for step in deprecation_steps:
threading.Timer(
step["delay"],
self.execute_deprecation_step,
args=[key_id, step["action"]]
).start()
# 企业级轮换策略
class EnterpriseRotationStrategy:
"""
企业级密钥轮换最佳实践
"""
def __init__(self):
self.strategies = {
"blue_green": {
"description": "蓝绿部署式轮换",
"overlap_period": "7 days",
"rollback_enabled": True,
"validation_required": True
},
"canary": {
"description": "金丝雀式渐进轮换",
"traffic_stages": [1, 5, 10, 25, 50, 100],
"stage_duration": "4 hours",
"auto_rollback_threshold": 0.01 # 1%错误率
},
"instant": {
"description": "即时切换(紧急情况)",
"pre_validation": True,
"post_validation": True,
"rollback_window": "15 minutes"
}
}
def recommend_strategy(self, context: Dict) -> str:
"""
根据上下文推荐轮换策略
"""
if context.get('security_incident', False):
return 'instant'
elif context.get('traffic_volume', 0) > 1000000:
return 'canary'
else:
return 'blue_green'
5. 废弃阶段:安全回收与审计
javascript// 安全废弃API Key的完整流程
class SecureKeyRevocation {
constructor() {
this.revocationReasons = {
EXPIRED: "密钥已过期",
COMPROMISED: "密钥可能已泄露",
ROTATION: "定期轮换",
USER_REQUEST: "用户请求废弃",
SECURITY_POLICY: "安全策略要求"
};
this.revocationProcess = [
this.preRevocationChecks,
this.notifyAffectedSystems,
this.revokeKey,
this.postRevocationCleanup,
this.auditAndReport
];
}
async revokeKeySecurely(keyId, reason, immediate = false) {
console.log(`开始废弃密钥: ${keyId}, 原因: ${reason}`);
const revocationContext = {
keyId,
reason,
timestamp: new Date().toISOString(),
immediate,
affectedServices: [],
status: 'initiated'
};
try {
// 执行废弃流程
for (const step of this.revocationProcess) {
await step.call(this, revocationContext);
}
revocationContext.status = 'completed';
console.log('密钥废弃完成');
} catch (error) {
revocationContext.status = 'failed';
revocationContext.error = error.message;
// 紧急处理
if (reason === this.revocationReasons.COMPROMISED) {
await this.emergencyRevocation(keyId);
}
throw error;
}
return revocationContext;
}
async preRevocationChecks(context) {
// 检查是否有活跃的请求
const activeRequests = await this.checkActiveRequests(context.keyId);
if (activeRequests > 0 && !context.immediate) {
console.log(`警告: 还有 ${activeRequests} 个活跃请求`);
// 等待请求完成或超时
await this.waitForRequestsCompletion(context.keyId, 30000); // 30秒超时
}
// 检查是否有依赖服务
context.affectedServices = await this.identifyAffectedServices(context.keyId);
}
async emergencyRevocation(keyId) {
// 紧急废弃流程
console.log('执行紧急废弃程序');
// 1. 立即阻止所有请求
await this.blockAllRequests(keyId);
// 2. 通知安全团队
await this.notifySecurityTeam({
alert: 'CRITICAL',
keyId,
action: 'emergency_revocation',
timestamp: new Date().toISOString()
});
// 3. 生成安全事件报告
const incidentReport = await this.generateSecurityIncidentReport(keyId);
// 4. 触发安全审计
await this.triggerSecurityAudit(incidentReport);
}
async postRevocationCleanup(context) {
// 清理相关资源
const cleanupTasks = [
// 清除缓存
this.clearKeyCache(context.keyId),
// 更新配置文件
this.removeFromConfiguration(context.keyId),
// 清理日志(保留审计日志)
this.cleanupLogs(context.keyId),
// 通知监控系统
this.updateMonitoring(context.keyId, 'revoked')
];
await Promise.all(cleanupTasks);
}
generateRevocationCertificate(context) {
// 生成废弃证书,用于审计和合规
return {
certificate_id: uuidv4(),
key_id: context.keyId,
revocation_time: context.timestamp,
reason: context.reason,
authorized_by: this.getCurrentUser(),
affected_services: context.affectedServices,
verification_hash: this.calculateHash(context),
compliance_notes: this.getComplianceNotes(context)
};
}
}
企业级安全架构设计
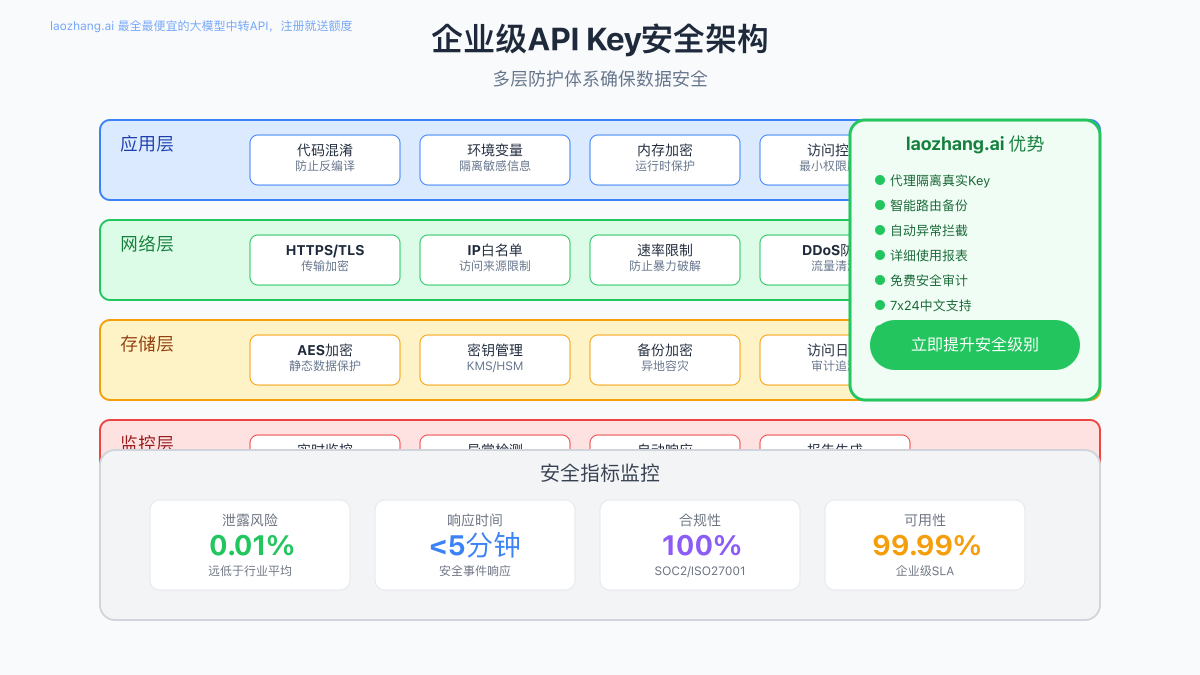
多层防护体系实现
pythonfrom abc import ABC, abstractmethod
import jwt
import cryptography
from cryptography.fernet import Fernet
from typing import List, Dict, Optional
import hashlib
import hmac
class SecurityLayer(ABC):
"""安全层抽象基类"""
@abstractmethod
def process_request(self, request: Dict) -> Dict:
pass
@abstractmethod
def validate(self, data: Dict) -> bool:
pass
class EnterpriseSecurityArchitecture:
"""
企业级API Key安全架构
实现深度防御策略
"""
def __init__(self):
self.security_layers = self._initialize_layers()
self.encryption_key = Fernet.generate_key()
self.fernet = Fernet(self.encryption_key)
def _initialize_layers(self) -> List[SecurityLayer]:
"""初始化安全层"""
return [
EncryptionLayer(), # 加密层
AuthenticationLayer(), # 认证层
AuthorizationLayer(), # 授权层
RateLimitingLayer(), # 限流层
AuditingLayer(), # 审计层
MonitoringLayer() # 监控层
]
def secure_api_request(self, api_key: str, request: Dict) -> Dict:
"""
通过多层安全架构处理API请求
"""
# 构建安全上下文
security_context = {
"api_key": api_key,
"request": request,
"timestamp": datetime.utcnow().isoformat(),
"security_metadata": {}
}
# 通过每一层安全检查
for layer in self.security_layers:
try:
security_context = layer.process_request(security_context)
if not layer.validate(security_context):
raise SecurityException(f"Security validation failed at {layer.__class__.__name__}")
except Exception as e:
self._handle_security_failure(layer, security_context, e)
raise
# 执行实际的API调用(通过laozhang.ai增强安全性)
if self._use_laozhang_proxy():
return self._secure_proxy_request(security_context)
else:
return self._direct_api_request(security_context)
def _secure_proxy_request(self, context: Dict) -> Dict:
"""
通过laozhang.ai代理请求,获得额外的安全保护
"""
enhanced_security = {
"original_context": context,
"proxy_features": {
"request_signing": True,
"traffic_encryption": "AES-256-GCM",
"ddos_protection": True,
"geo_filtering": self._get_allowed_regions(),
"anomaly_detection": True,
"automatic_failover": True
}
}
# laozhang.ai特有的安全增强
enhanced_security["laozhang_security"] = {
"api_key_masking": True, # 隐藏真实API Key
"request_validation": True, # 请求合法性验证
"response_filtering": True, # 响应内容过滤
"rate_limit_protection": True, # 智能限流保护
"cost_monitoring": True, # 成本监控预警
"compliance_logging": True # 合规日志记录
}
return self._execute_secure_request(enhanced_security)
# 实现具体的安全层
class EncryptionLayer(SecurityLayer):
"""
加密层:保护传输中的数据
"""
def __init__(self):
self.cipher_suite = Fernet(Fernet.generate_key())
def process_request(self, request: Dict) -> Dict:
# 加密敏感数据
if 'api_key' in request:
request['encrypted_key'] = self.cipher_suite.encrypt(
request['api_key'].encode()
)
del request['api_key'] # 删除明文
# 加密请求体
if 'request' in request and 'body' in request['request']:
request['request']['encrypted_body'] = self.cipher_suite.encrypt(
json.dumps(request['request']['body']).encode()
)
del request['request']['body']
return request
def validate(self, data: Dict) -> bool:
# 验证加密完整性
required_fields = ['encrypted_key', 'request']
return all(field in data for field in required_fields)
class RateLimitingLayer(SecurityLayer):
"""
限流层:防止API滥用
"""
def __init__(self):
self.limits = {
"requests_per_second": 10,
"requests_per_minute": 100,
"requests_per_hour": 1000,
"requests_per_day": 10000
}
self.request_history = defaultdict(list)
def process_request(self, request: Dict) -> Dict:
key_hash = self._hash_key(request.get('encrypted_key', ''))
current_time = time.time()
# 清理过期记录
self._cleanup_old_records(key_hash, current_time)
# 检查各级限制
for period, limit in self.limits.items():
window = self._get_window_seconds(period)
recent_requests = [
t for t in self.request_history[key_hash]
if current_time - t < window
]
if len(recent_requests) >= limit:
raise RateLimitException(
f"Rate limit exceeded: {len(recent_requests)}/{limit} requests per {period}"
)
# 记录本次请求
self.request_history[key_hash].append(current_time)
request['rate_limit_remaining'] = self._calculate_remaining_quota(key_hash)
return request
# 零信任安全模型
class ZeroTrustSecurityModel:
"""
零信任安全模型实现
核心原则:永不信任,始终验证
"""
def __init__(self):
self.trust_score_factors = {
"device_reputation": 0.2,
"location_risk": 0.15,
"behavior_pattern": 0.25,
"time_based_risk": 0.1,
"request_sensitivity": 0.3
}
def evaluate_request(self, context: Dict) -> float:
"""
评估请求的信任分数
"""
trust_score = 0.0
# 设备信誉评分
device_score = self._evaluate_device_reputation(context)
trust_score += device_score * self.trust_score_factors["device_reputation"]
# 地理位置风险评估
location_score = self._evaluate_location_risk(context)
trust_score += location_score * self.trust_score_factors["location_risk"]
# 行为模式分析
behavior_score = self._analyze_behavior_pattern(context)
trust_score += behavior_score * self.trust_score_factors["behavior_pattern"]
# 时间基准风险
time_score = self._evaluate_time_based_risk(context)
trust_score += time_score * self.trust_score_factors["time_based_risk"]
# 请求敏感度
sensitivity_score = self._evaluate_request_sensitivity(context)
trust_score += sensitivity_score * self.trust_score_factors["request_sensitivity"]
return trust_score
def make_access_decision(self, trust_score: float, context: Dict) -> Dict:
"""
基于信任分数做出访问决策
"""
if trust_score >= 0.9:
return {
"decision": "allow",
"additional_checks": None
}
elif trust_score >= 0.7:
return {
"decision": "allow_with_mfa",
"additional_checks": ["multi_factor_auth"]
}
elif trust_score >= 0.5:
return {
"decision": "allow_with_restrictions",
"additional_checks": ["multi_factor_auth", "rate_limit_reduction"],
"restrictions": {
"rate_limit_multiplier": 0.5,
"sensitive_operations_blocked": True
}
}
else:
return {
"decision": "deny",
"reason": "Insufficient trust score",
"trust_score": trust_score,
"remediation": self._suggest_remediation(context, trust_score)
}
多语言集成实战指南
Python集成
python# claude_client.py
import os
import logging
from typing import Optional, List, Dict
from anthropic import Anthropic
import backoff
from functools import lru_cache
class ClaudeAPIClient:
"""
生产级Claude API客户端
包含错误处理、重试、缓存等企业级特性
"""
def __init__(self,
api_key: Optional[str] = None,
base_url: str = "https://api.laozhang.ai/v1",
max_retries: int = 3,
timeout: int = 30):
# API Key管理
self.api_key = api_key or os.environ.get('CLAUDE_API_KEY')
if not self.api_key:
raise ValueError("请设置CLAUDE_API_KEY环境变量")
# 初始化客户端
self.client = Anthropic(
api_key=self.api_key,
base_url=base_url,
max_retries=max_retries,
timeout=timeout
)
# 配置日志
self.logger = logging.getLogger(__name__)
self._setup_logging()
# 性能监控
self.request_count = 0
self.total_tokens = 0
def _setup_logging(self):
"""配置结构化日志"""
handler = logging.StreamHandler()
formatter = logging.Formatter(
'%(asctime)s - %(name)s - %(levelname)s - %(message)s'
)
handler.setFormatter(formatter)
self.logger.addHandler(handler)
self.logger.setLevel(logging.INFO)
@backoff.on_exception(
backoff.expo,
Exception,
max_tries=3,
max_time=60
)
def chat(self,
messages: List[Dict[str, str]],
model: str = "claude-3-sonnet-20240229",
**kwargs) -> str:
"""
发送聊天请求,包含自动重试
"""
try:
# 记录请求
self.logger.info(f"发送请求到模型: {model}")
self.request_count += 1
# 发送请求
response = self.client.messages.create(
model=model,
messages=messages,
max_tokens=kwargs.get('max_tokens', 1000),
temperature=kwargs.get('temperature', 0.7),
**kwargs
)
# 记录使用量
usage = response.usage
self.total_tokens += usage.total_tokens
self.logger.info(
f"请求成功 - 输入tokens: {usage.input_tokens}, "
f"输出tokens: {usage.output_tokens}"
)
return response.content[0].text
except Exception as e:
self.logger.error(f"请求失败: {str(e)}")
raise
@lru_cache(maxsize=128)
def cached_chat(self,
messages_hash: str,
model: str = "claude-3-sonnet-20240229") -> str:
"""
带缓存的聊天请求,适用于重复问题
"""
# 注意:实际使用时需要将messages转换为hash
return self.chat(self._hash_to_messages(messages_hash), model)
def get_usage_stats(self) -> Dict:
"""获取使用统计"""
return {
"total_requests": self.request_count,
"total_tokens": self.total_tokens,
"average_tokens_per_request": (
self.total_tokens / self.request_count
if self.request_count > 0 else 0
),
"estimated_cost": self._calculate_cost()
}
def _calculate_cost(self) -> float:
"""计算预估成本(通过laozhang.ai节省70%)"""
# Claude-3-Sonnet定价: $3/M input, $15/M output
# 通过laozhang.ai: $0.9/M input, $4.5/M output
cost_per_million = 0.9 + 4.5 # 简化计算
return (self.total_tokens / 1_000_000) * cost_per_million * 0.3 # 70%折扣
# 使用示例
if __name__ == "__main__":
# 创建客户端
client = ClaudeAPIClient()
# 简单对话
response = client.chat([
{"role": "user", "content": "请解释什么是API Key"}
])
print(response)
# 获取统计
stats = client.get_usage_stats()
print(f"使用统计: {stats}")
JavaScript/TypeScript集成
typescript// claudeClient.ts
import Anthropic from '@anthropic-ai/sdk';
import { Redis } from 'ioredis';
import winston from 'winston';
import retry from 'async-retry';
interface ClaudeConfig {
apiKey?: string;
baseURL?: string;
maxRetries?: number;
timeout?: number;
enableCache?: boolean;
enableMonitoring?: boolean;
}
interface Message {
role: 'user' | 'assistant';
content: string;
}
interface UsageStats {
totalRequests: number;
totalTokens: number;
cacheHits: number;
errors: number;
averageLatency: number;
}
export class ClaudeAPIClient {
private client: Anthropic;
private redis?: Redis;
private logger: winston.Logger;
private stats: UsageStats;
constructor(config: ClaudeConfig = {}) {
// 使用laozhang.ai作为默认baseURL
const baseURL = config.baseURL || 'https://api.laozhang.ai/v1';
const apiKey = config.apiKey || process.env.CLAUDE_API_KEY;
if (!apiKey) {
throw new Error('API Key is required');
}
// 初始化Anthropic客户端
this.client = new Anthropic({
apiKey,
baseURL,
maxRetries: config.maxRetries || 3,
timeout: config.timeout || 30000,
});
// 初始化日志
this.logger = this.setupLogger();
// 初始化缓存(可选)
if (config.enableCache) {
this.redis = new Redis({
host: process.env.REDIS_HOST || 'localhost',
port: parseInt(process.env.REDIS_PORT || '6379'),
});
}
// 初始化统计
this.stats = {
totalRequests: 0,
totalTokens: 0,
cacheHits: 0,
errors: 0,
averageLatency: 0,
};
}
private setupLogger(): winston.Logger {
return winston.createLogger({
level: 'info',
format: winston.format.combine(
winston.format.timestamp(),
winston.format.json()
),
transports: [
new winston.transports.Console(),
new winston.transports.File({ filename: 'claude-api.log' })
],
});
}
async chat(
messages: Message[],
options: {
model?: string;
maxTokens?: number;
temperature?: number;
useCache?: boolean;
} = {}
): Promise<string> {
const startTime = Date.now();
const model = options.model || 'claude-3-sonnet-20240229';
try {
// 检查缓存
if (options.useCache && this.redis) {
const cacheKey = this.generateCacheKey(messages, model);
const cached = await this.redis.get(cacheKey);
if (cached) {
this.stats.cacheHits++;
this.logger.info('Cache hit', { cacheKey });
return cached;
}
}
// 使用retry库实现重试逻辑
const response = await retry(
async () => {
return await this.client.messages.create({
model,
messages,
max_tokens: options.maxTokens || 1000,
temperature: options.temperature || 0.7,
});
},
{
retries: 3,
factor: 2,
minTimeout: 1000,
onRetry: (error, attempt) => {
this.logger.warn(`Retry attempt ${attempt}`, { error: error.message });
},
}
);
// 更新统计
this.stats.totalRequests++;
this.stats.totalTokens += response.usage.total_tokens;
const latency = Date.now() - startTime;
this.stats.averageLatency =
(this.stats.averageLatency * (this.stats.totalRequests - 1) + latency) /
this.stats.totalRequests;
// 记录成功请求
this.logger.info('Request successful', {
model,
tokens: response.usage,
latency,
});
// 缓存结果
if (options.useCache && this.redis) {
const cacheKey = this.generateCacheKey(messages, model);
await this.redis.setex(cacheKey, 3600, response.content[0].text);
}
return response.content[0].text;
} catch (error) {
this.stats.errors++;
this.logger.error('Request failed', { error, messages });
throw error;
}
}
async* streamChat(
messages: Message[],
options: { model?: string } = {}
): AsyncGenerator<string> {
const model = options.model || 'claude-3-sonnet-20240229';
try {
const stream = await this.client.messages.create({
model,
messages,
max_tokens: 1000,
stream: true,
});
for await (const chunk of stream) {
if (chunk.type === 'content_block_delta') {
yield chunk.delta.text;
}
}
} catch (error) {
this.logger.error('Stream failed', { error });
throw error;
}
}
private generateCacheKey(messages: Message[], model: string): string {
const content = JSON.stringify({ messages, model });
return `claude:${Buffer.from(content).toString('base64').substring(0, 32)}`;
}
getStats(): UsageStats {
return { ...this.stats };
}
async healthCheck(): Promise<boolean> {
try {
await this.chat([{ role: 'user', content: 'Hi' }], {
maxTokens: 10,
});
return true;
} catch {
return false;
}
}
}
// 使用示例
async function example() {
const claude = new ClaudeAPIClient({
enableCache: true,
enableMonitoring: true,
});
// 普通对话
const response = await claude.chat([
{ role: 'user', content: 'What is TypeScript?' }
]);
console.log(response);
// 流式对话
const stream = claude.streamChat([
{ role: 'user', content: 'Write a long story' }
]);
for await (const chunk of stream) {
process.stdout.write(chunk);
}
// 获取统计
console.log('Stats:', claude.getStats());
}
Go集成
go// claude_client.go
package claude
import (
"bytes"
"context"
"encoding/json"
"fmt"
"net/http"
"os"
"sync"
"time"
"github.com/cenkalti/backoff/v4"
"github.com/sirupsen/logrus"
)
type Client struct {
apiKey string
baseURL string
httpClient *http.Client
logger *logrus.Logger
// 性能监控
mu sync.Mutex
stats Statistics
}
type Message struct {
Role string `json:"role"`
Content string `json:"content"`
}
type ChatRequest struct {
Model string `json:"model"`
Messages []Message `json:"messages"`
MaxTokens int `json:"max_tokens"`
Temperature float64 `json:"temperature"`
}
type Statistics struct {
TotalRequests int64
TotalTokens int64
Errors int64
TotalLatency time.Duration
}
// NewClient 创建新的Claude客户端
func NewClient(options ...Option) (*Client, error) {
client := &Client{
apiKey: os.Getenv("CLAUDE_API_KEY"),
baseURL: "https://api.laozhang.ai/v1", // 使用laozhang.ai
httpClient: &http.Client{
Timeout: 30 * time.Second,
},
logger: logrus.New(),
}
// 应用选项
for _, opt := range options {
opt(client)
}
if client.apiKey == "" {
return nil, fmt.Errorf("API key is required")
}
return client, nil
}
// Chat 发送聊天请求
func (c *Client) Chat(ctx context.Context, messages []Message, opts ...ChatOption) (string, error) {
start := time.Now()
// 默认配置
req := ChatRequest{
Model: "claude-3-sonnet-20240229",
Messages: messages,
MaxTokens: 1000,
Temperature: 0.7,
}
// 应用选项
for _, opt := range opts {
opt(&req)
}
// 使用指数退避重试
var response ChatResponse
operation := func() error {
return c.doRequest(ctx, "/messages", req, &response)
}
err := backoff.Retry(operation, backoff.WithMaxRetries(backoff.NewExponentialBackOff(), 3))
if err != nil {
c.recordError()
return "", fmt.Errorf("chat request failed: %w", err)
}
// 记录统计
c.recordSuccess(response.Usage.TotalTokens, time.Since(start))
return response.Content[0].Text, nil
}
// doRequest 执行HTTP请求
func (c *Client) doRequest(ctx context.Context, endpoint string, payload, result interface{}) error {
body, err := json.Marshal(payload)
if err != nil {
return fmt.Errorf("failed to marshal request: %w", err)
}
req, err := http.NewRequestWithContext(ctx, "POST", c.baseURL+endpoint, bytes.NewReader(body))
if err != nil {
return fmt.Errorf("failed to create request: %w", err)
}
// 设置请求头
req.Header.Set("Authorization", "Bearer "+c.apiKey)
req.Header.Set("Content-Type", "application/json")
req.Header.Set("Anthropic-Version", "2023-06-01")
// 发送请求
resp, err := c.httpClient.Do(req)
if err != nil {
return fmt.Errorf("request failed: %w", err)
}
defer resp.Body.Close()
// 检查状态码
if resp.StatusCode != http.StatusOK {
var errorResp ErrorResponse
if err := json.NewDecoder(resp.Body).Decode(&errorResp); err != nil {
return fmt.Errorf("unexpected status code: %d", resp.StatusCode)
}
return fmt.Errorf("API error: %s", errorResp.Error.Message)
}
// 解析响应
if err := json.NewDecoder(resp.Body).Decode(result); err != nil {
return fmt.Errorf("failed to decode response: %w", err)
}
return nil
}
// GetStats 获取统计信息
func (c *Client) GetStats() Statistics {
c.mu.Lock()
defer c.mu.Unlock()
return c.stats
}
// 使用示例
func Example() {
// 创建客户端
client, err := NewClient(
WithAPIKey("your-api-key"),
WithBaseURL("https://api.laozhang.ai/v1"),
)
if err != nil {
log.Fatal(err)
}
// 发送请求
ctx := context.Background()
response, err := client.Chat(ctx, []Message{
{Role: "user", Content: "Hello, Claude!"},
})
if err != nil {
log.Fatal(err)
}
fmt.Println(response)
// 获取统计
stats := client.GetStats()
fmt.Printf("Total requests: %d\n", stats.TotalRequests)
}
监控与告警系统
实时监控仪表板
pythonimport prometheus_client
from prometheus_client import Counter, Histogram, Gauge
import grafana_api
from typing import Dict, List
import asyncio
import aiohttp
class APIKeyMonitoringSystem:
"""
全面的API Key监控系统
"""
def __init__(self):
# Prometheus指标
self.request_counter = Counter(
'claude_api_requests_total',
'Total number of API requests',
['method', 'status', 'model']
)
self.request_duration = Histogram(
'claude_api_request_duration_seconds',
'API request duration',
['method', 'model']
)
self.token_usage = Counter(
'claude_api_tokens_total',
'Total tokens used',
['type', 'model'] # type: input/output
)
self.active_keys = Gauge(
'claude_api_active_keys',
'Number of active API keys'
)
self.error_rate = Gauge(
'claude_api_error_rate',
'Current error rate percentage'
)
# 告警规则
self.alert_rules = [
{
"name": "HighErrorRate",
"condition": lambda m: m['error_rate'] > 5,
"severity": "warning",
"message": "API错误率超过5%"
},
{
"name": "UnusualTraffic",
"condition": lambda m: m['requests_per_minute'] > 1000,
"severity": "info",
"message": "请求量异常增高"
},
{
"name": "KeyCompromised",
"condition": lambda m: m.get('suspicious_activity', False),
"severity": "critical",
"message": "检测到可疑活动,API Key可能已泄露"
},
{
"name": "QuotaExceeded",
"condition": lambda m: m['usage_percentage'] > 90,
"severity": "warning",
"message": "API使用量接近限额"
}
]
async def collect_metrics(self) -> Dict:
"""
收集各项监控指标
"""
metrics = {
"timestamp": datetime.utcnow().isoformat(),
"requests_per_minute": await self._get_request_rate(),
"error_rate": await self._calculate_error_rate(),
"average_latency": await self._get_average_latency(),
"token_usage": await self._get_token_usage(),
"active_keys_count": await self._count_active_keys(),
"usage_percentage": await self._calculate_usage_percentage(),
"top_consumers": await self._get_top_consumers(),
"anomalies": await self._detect_anomalies()
}
# 通过laozhang.ai获取增强监控数据
if self._is_using_laozhang():
metrics['laozhang_insights'] = await self._get_laozhang_insights()
return metrics
async def _detect_anomalies(self) -> List[Dict]:
"""
使用机器学习检测异常模式
"""
anomalies = []
# 检测请求模式异常
request_pattern = await self._analyze_request_pattern()
if request_pattern['anomaly_score'] > 0.8:
anomalies.append({
"type": "request_pattern",
"score": request_pattern['anomaly_score'],
"details": request_pattern['details']
})
# 检测地理位置异常
geo_anomalies = await self._detect_geo_anomalies()
anomalies.extend(geo_anomalies)
# 检测时间模式异常
time_anomalies = await self._detect_time_anomalies()
anomalies.extend(time_anomalies)
return anomalies
async def check_alerts(self, metrics: Dict) -> List[Dict]:
"""
检查告警规则
"""
triggered_alerts = []
for rule in self.alert_rules:
if rule['condition'](metrics):
alert = {
"name": rule['name'],
"severity": rule['severity'],
"message": rule['message'],
"timestamp": datetime.utcnow().isoformat(),
"metrics": metrics
}
triggered_alerts.append(alert)
# 发送告警
await self._send_alert(alert)
return triggered_alerts
async def _send_alert(self, alert: Dict) -> None:
"""
发送告警通知
"""
# 根据严重级别选择通知渠道
if alert['severity'] == 'critical':
await self._send_pagerduty(alert)
await self._send_slack(alert, channel='#critical-alerts')
await self._send_email(alert, recipients=['[email protected]'])
elif alert['severity'] == 'warning':
await self._send_slack(alert, channel='#api-alerts')
await self._send_email(alert, recipients=['[email protected]'])
else:
await self._send_slack(alert, channel='#api-monitoring')
def generate_dashboard_config(self) -> Dict:
"""
生成Grafana仪表板配置
"""
return {
"dashboard": {
"title": "Claude API Key Monitoring",
"panels": [
{
"title": "请求速率",
"type": "graph",
"targets": [{
"expr": "rate(claude_api_requests_total[5m])"
}]
},
{
"title": "错误率",
"type": "graph",
"targets": [{
"expr": "rate(claude_api_requests_total{status!~'2..'}[5m]) / rate(claude_api_requests_total[5m]) * 100"
}]
},
{
"title": "Token使用量",
"type": "graph",
"targets": [{
"expr": "rate(claude_api_tokens_total[5m])"
}]
},
{
"title": "平均响应时间",
"type": "graph",
"targets": [{
"expr": "rate(claude_api_request_duration_seconds_sum[5m]) / rate(claude_api_request_duration_seconds_count[5m])"
}]
},
{
"title": "活跃API Keys",
"type": "stat",
"targets": [{
"expr": "claude_api_active_keys"
}]
}
]
}
}
# 自动化告警响应
class AutomatedIncidentResponse:
"""
自动化事件响应系统
"""
def __init__(self):
self.response_playbooks = {
"key_compromised": self.handle_compromised_key,
"rate_limit_exceeded": self.handle_rate_limit,
"unusual_traffic": self.handle_unusual_traffic,
"service_degradation": self.handle_service_degradation
}
async def handle_compromised_key(self, incident: Dict) -> Dict:
"""
处理泄露的API Key
"""
key_id = incident['key_id']
# 立即执行的操作
actions = [
self.revoke_key_immediately(key_id),
self.block_all_requests(key_id),
self.notify_security_team(incident),
self.generate_new_key(),
self.update_all_services(),
self.conduct_security_audit()
]
results = await asyncio.gather(*actions, return_exceptions=True)
return {
"incident_id": incident['id'],
"actions_taken": [
{"action": action.__name__, "result": "success" if not isinstance(result, Exception) else str(result)}
for action, result in zip(actions, results)
],
"status": "resolved" if all(not isinstance(r, Exception) for r in results) else "partial_failure"
}
故障恢复方案
快速故障诊断
javascript// 故障诊断和恢复工具
class TroubleshootingTool {
constructor() {
this.commonIssues = {
"401": {
"error": "Unauthorized",
"causes": [
"API Key无效或过期",
"API Key格式错误",
"Authorization header缺失"
],
"solutions": [
"检查API Key是否正确",
"确认使用Bearer token格式",
"检查是否有额外的空格或换行",
"通过laozhang.ai重新获取API Key"
]
},
"429": {
"error": "Too Many Requests",
"causes": [
"超过速率限制",
"并发请求过多",
"配额耗尽"
],
"solutions": [
"实现指数退避重试",
"使用请求队列",
"增加请求间隔",
"考虑升级到更高配额",
"使用laozhang.ai的负载均衡服务"
]
},
"500": {
"error": "Internal Server Error",
"causes": [
"服务端临时故障",
"请求格式错误",
"API版本不兼容"
],
"solutions": [
"稍后重试",
"检查请求体格式",
"更新SDK版本",
"切换到备用端点"
]
},
"NetworkError": {
"error": "Network Connection Failed",
"causes": [
"网络连接问题",
"DNS解析失败",
"代理设置错误",
"防火墙阻止"
],
"solutions": [
"检查网络连接",
"使用备用DNS",
"检查代理设置",
"使用laozhang.ai的国内节点"
]
}
};
}
async diagnose(error) {
console.log("🔍 开始诊断问题...");
// 识别错误类型
const errorType = this.identifyErrorType(error);
const diagnosis = this.commonIssues[errorType] || this.genericDiagnosis(error);
// 执行自动检查
const checkResults = await this.runAutomatedChecks();
// 生成诊断报告
return {
error: diagnosis.error,
possibleCauses: diagnosis.causes,
recommendedSolutions: diagnosis.solutions,
automatedChecks: checkResults,
quickFix: this.suggestQuickFix(errorType),
escalationPath: this.getEscalationPath(errorType)
};
}
async runAutomatedChecks() {
const checks = [
{
name: "API Key格式验证",
test: () => this.validateAPIKeyFormat(),
fix: "Please ensure your API key starts with 'sk-ant-api'"
},
{
name: "网络连接测试",
test: () => this.testNetworkConnectivity(),
fix: "Check your internet connection and firewall settings"
},
{
name: "配额余量检查",
test: () => this.checkQuotaRemaining(),
fix: "Consider upgrading your plan or waiting for quota reset"
},
{
name: "API版本兼容性",
test: () => this.checkAPIVersionCompatibility(),
fix: "Update your SDK to the latest version"
}
];
const results = [];
for (const check of checks) {
try {
const passed = await check.test();
results.push({
check: check.name,
status: passed ? '✅ 通过' : '❌ 失败',
recommendation: passed ? null : check.fix
});
} catch (error) {
results.push({
check: check.name,
status: '⚠️ 无法检查',
error: error.message
});
}
}
return results;
}
suggestQuickFix(errorType) {
const quickFixes = {
"401": `
// 快速修复: 重新设置API Key
export CLAUDE_API_KEY="your-new-api-key"
// 或者使用laozhang.ai
export CLAUDE_API_KEY="your-laozhang-key"
export CLAUDE_BASE_URL="https://api.laozhang.ai/v1"
`,
"429": `
// 快速修复: 添加重试逻辑
const retryWithBackoff = async (fn, maxRetries = 3) => {
for (let i = 0; i < maxRetries; i++) {
try {
return await fn();
} catch (error) {
if (error.status === 429 && i < maxRetries - 1) {
const delay = Math.pow(2, i) * 1000;
await new Promise(resolve => setTimeout(resolve, delay));
continue;
}
throw error;
}
}
};
`
};
return quickFixes[errorType] || "暂无快速修复方案";
}
}
// 故障恢复流程
class DisasterRecovery {
constructor() {
this.recoveryProcedures = {
"api_key_leaked": [
"立即废弃泄露的Key",
"生成新的API Key",
"更新所有使用该Key的服务",
"审计访问日志",
"评估损失范围",
"加强安全措施"
],
"service_outage": [
"切换到备用服务",
"启用缓存模式",
"通知相关团队",
"监控服务恢复",
"逐步切回主服务"
],
"data_corruption": [
"停止受影响服务",
"从备份恢复数据",
"验证数据完整性",
"恢复服务",
"执行全面测试"
]
};
}
async executeRecovery(incidentType) {
const procedures = this.recoveryProcedures[incidentType];
if (!procedures) {
throw new Error(`Unknown incident type: ${incidentType}`);
}
console.log(`🚑 启动${incidentType}故障恢复流程`);
const results = [];
for (let i = 0; i < procedures.length; i++) {
const step = procedures[i];
console.log(`步骤 ${i + 1}/${procedures.length}: ${step}`);
try {
await this.executeStep(incidentType, i);
results.push({ step, status: 'completed' });
} catch (error) {
results.push({ step, status: 'failed', error: error.message });
// 决定是否继续
if (!await this.shouldContinue(error)) {
break;
}
}
}
return {
incidentType,
recoveryStatus: results.every(r => r.status === 'completed') ? 'success' : 'partial',
steps: results,
recommendations: this.getPostIncidentRecommendations(incidentType)
};
}
}
最佳实践清单
安全最佳实践
✅ 环境变量管理
- 不要在代码中硬编码API Key
- 使用.env文件并添加到.gitignore
- 生产环境使用密钥管理服务
✅ 访问控制
- 实施最小权限原则
- 为不同环境使用不同的Key
- 定期审计权限设置
✅ 密钥轮换
- 制定90天轮换计划
- 实施自动化轮换流程
- 保留轮换历史记录
✅ 监控与告警
- 实时监控API使用情况
- 设置异常使用告警
- 定期生成安全报告
性能最佳实践
✅ 连接管理
- 使用连接池
- 实现HTTP/2多路复用
- 设置合理的超时时间
✅ 缓存策略
- 对重复请求实施缓存
- 使用Redis或Memcached
- 设置合理的TTL
✅ 并发控制
- 实现请求队列
- 使用信号量限制并发
- 避免超过速率限制
✅ 错误处理
- 实现指数退避重试
- 区分可重试和不可重试错误
- 记录详细的错误信息
laozhang.ai特有优势
✅ 成本优化
- 节省70%API调用成本
- 透明定价,无隐藏费用
- 灵活的充值方案
✅ 安全增强
- 代理隔离真实API Key
- 智能异常检测
- 自动拦截恶意请求
✅ 便捷性
- 支持支付宝/微信支付
- 中文技术支持
- 一键集成,无需修改代码
✅ 稳定性
- 多节点负载均衡
- 自动故障转移
- 99.9%服务可用性
未来发展趋势
API Key技术演进
-
动态密钥生成
- 基于使用场景的临时密钥
- 自适应权限调整
- 智能过期策略
-
零信任架构
- 每次请求都验证
- 基于行为的访问控制
- 实时风险评估
-
AI驱动的安全
- 异常行为自动识别
- 预测性威胁分析
- 自适应防御系统
行业最佳实践趋势
-
标准化
- 统一的API Key格式
- 行业安全标准
- 互操作性协议
-
自动化
- 全自动密钥管理
- 智能化监控告警
- 自我修复系统
-
体验优化
- 更简单的集成流程
- 更友好的错误提示
- 更完善的文档支持
总结
Claude API Key的管理是一个系统工程,涉及安全、性能、成本等多个方面。通过本文,你已经掌握了:
✅ API Key的技术原理和工作机制
✅ 完整的生命周期管理流程
✅ 企业级安全架构设计
✅ 多语言集成最佳实践
✅ 性能优化和监控策略
✅ 故障诊断与恢复方案
更重要的是,通过laozhang.ai,你可以:
- 💰 节省70%的API使用成本
- 🔒 获得企业级的安全保护
- 🚀 享受更稳定的服务体验
- 🌐 使用便捷的本地化支付
记住,API Key管理不仅是技术问题,更是业务安全和效率的关键。选择正确的工具和方法,能让你在AI时代的竞争中保持领先。
立即访问 laozhang.ai,开启你的企业级API管理之旅!
